As the costs and risks of data breaches keep rising, cybersecurity should be a major focus for any B2B SaaS organization. As per IBM, the average cost of a data breach is $3.86 million. Organizations cannot afford to neglect security best practices when so much is at risk.
Salesforce is the major center of information for many SaaS firms, so it’s no wonder that organizations are concerned about the security of their Salesforce instance and interfaces. The good news is that Salesforce is a very secure platform.
Salesforce was designed from the ground up to safeguard your data and applications. However, there are several fundamental actions that all businesses must take in order to reduce external risks and breaches caused by human error or malicious intent.
In this blog, we will give you some essential tips and tricks to make your Salesforce organization more secure. Enroll with QuantoKnack’s Salesforce Admin Course, and you will be able to learn many more important aspects of the Salesforce platform.
5 Security Tips for How to Secure Your Salesforce Organization
Without further ado, let’s look at the five simple steps you can take to make your Salesforce org safer and more robust.
Start With A Salesforce Health Check
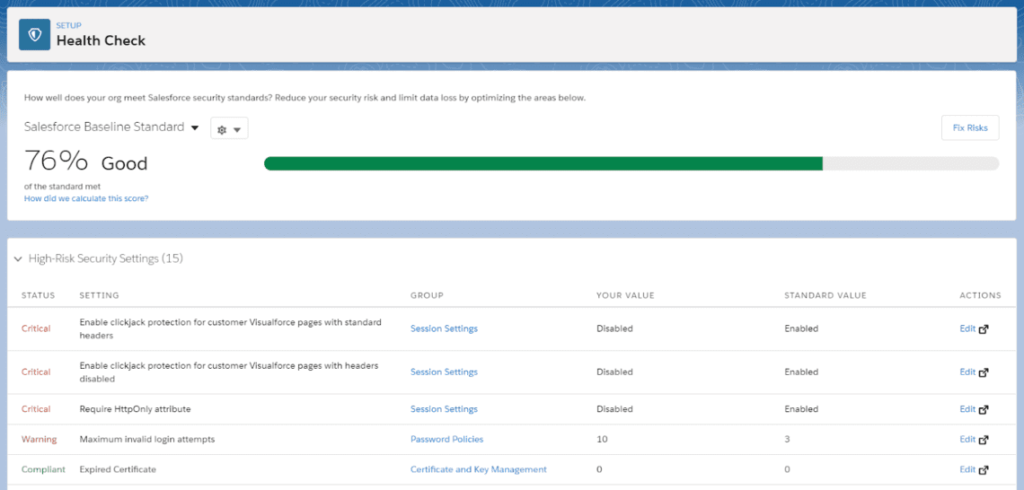
Salesforce’s native Health Check is a no-brainer if you need immediate wins. This useful feature compares your organization to Salesforce’s Security Baseline Standard and recommends resolving any vulnerabilities it identifies.
You may also upload your own security baseline standard and perform periodic checks against it. However, keep in mind that Salesforce has had 20 years to create theirs – and it is always being upgraded!
To do a health check on your organization, navigate to Setup > Security > Health Check.
Implement Two-Factor Authentication
Another effective method of data security is two-factor authentication. Every time a person logs in, they must go through two stages of authentication.
- Interfaces Logins
- Setting up two-factor authentication is a common approach to boost your instance’s security. In Salesforce, two-factor authentication may be used in two ways. The most fundamental method is to activate two-factor authentication for logins.
- This provides additional protection by requiring each user to authenticate their identity through an authentication App or text message/call every time they log in to your Org.
- For two-factor authentication, use the Salesforce Authenticator App.
- Two-Factor Authentication for Reports
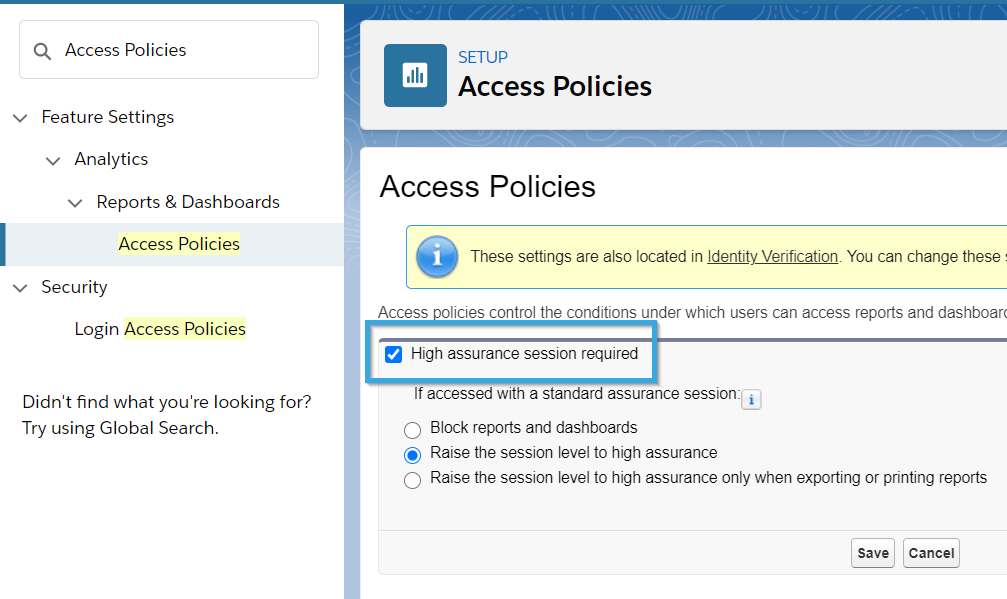
- Salesforce may also use two-factor authentication to safeguard report access. Users attempting to view reports will be prompted to authenticate their identity using two-factor authentication. To enable two-factor authentication for users viewing reports, the Admin(s) can “Raise the session level to High Assurance” in Setup.
Controlling Report Printing and Exporting Access
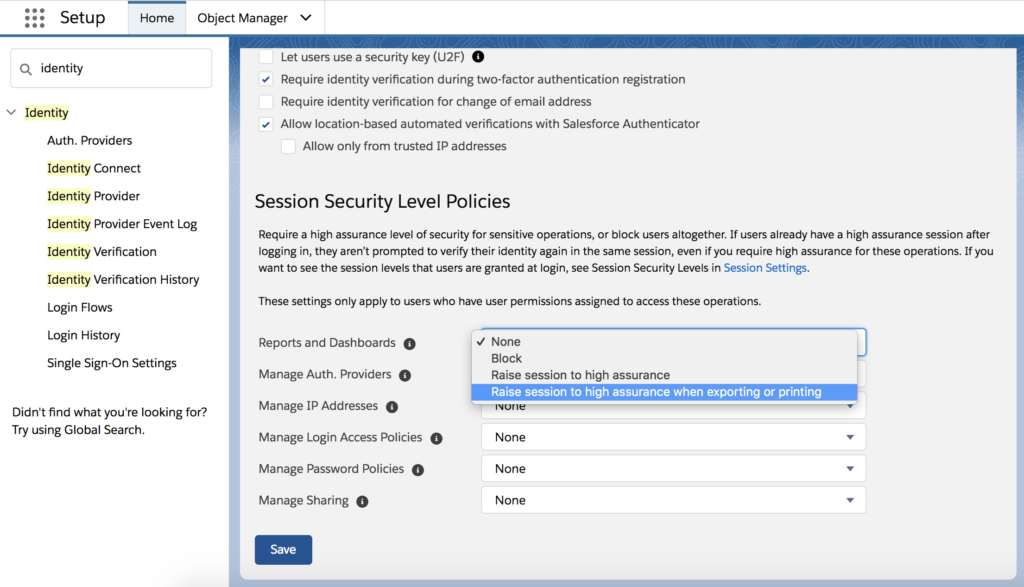
Salesforce may also be established to simply ask users to authenticate their identity when exporting or printing reports. To do this, under Setup, enter “Identity Verification” and activate “Raise the Session to High Assurance” under “Security Level Policies,” which will require users to log in when attempting to export data or view particular reports.
Ensure your Org is classified appropriately
Salesforce has advanced from a SaaS contact management solution to a much more powerful PaaS capable of supporting or delivering core business applications. While many businesses already understand how to manage the availability and security of these apps, we’ve seen that they frequently misclassify their Org, resulting in serious oversights. If a Salesforce Org is classified as “Type 1” or “Class A,” it should be regarded as such in terms of business continuity, disaster recovery, enterprise monitoring, security, and compliance.
Evaluate Your Custom Code Against OWASP Top 10
If you implement your own Salesforce code, you risk exposing a security hole that might eventually disclose critical information or allow malicious users to penetrate your system.
If you’re unsure where to begin assessing your code’s risk, check the OWASP Top 10.
The Open Web Application Security Project is committed to assisting in the creation of safe internet. Their list of top risks is based on real-world observations and is contributed by their large developer and system administrator community. As you integrate custom code into your environment, consider how it interacts with Salesforce and whether it exposes itself to vulnerabilities.
For example, “injection” is number three on the OWASP list of vulnerabilities. As a browser-based application, Salesforce must secure the attack surface from application code to the user interface. Cross-Site Scripting and SOSL/SOQL injection attacks are both OWASP Top 10 code vulnerabilities in the Salesforce environment.
This is an excellent place to start when examining and evaluating every line of code against a comprehensive and up-to-date list of vulnerabilities that may be prohibitive. More information about OWASP is available here.
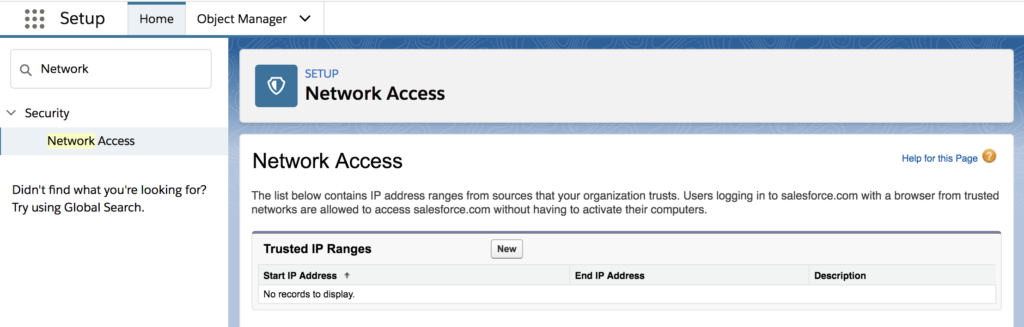
Set Up Trusted IP Ranges
Employees are increasingly signing into Salesforce from more places than ever before, which might expose them to risks. To address this, configure Trusted IP Ranges, which inform Salesforce which login locations are normal and which are suspect.
You may instruct Salesforce, for example, to trust your company’s office IP address and other specified workplace locations – and to challenge individuals logging in from any other addresses.
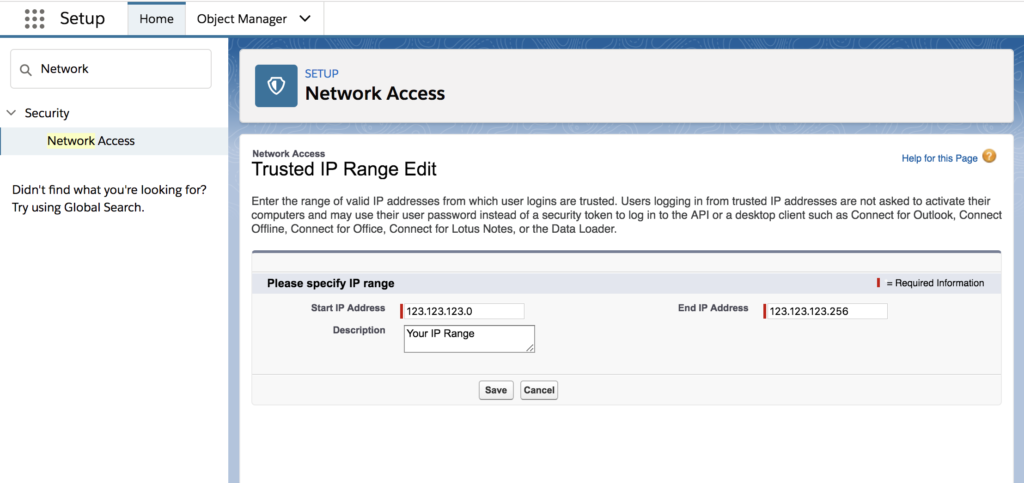
To add trusted IP ranges to your Salesforce security, go to Setup > Security > Network Access and provide a custom range of trusted addresses.
Profile-Based Trusted IP Addresses & Login Hours
You can modify trusted IP ranges depending on user profiles if you don’t need them to apply to your whole organization. For example, suppose you only want support users to be able to log in from your workplace network between the hours of 8 a.m. and 6 p.m., Monday through Friday.
That’s simple! Simply navigate to Setup > Users > Profiles, choose your Support profile, configure your IP ranges and log in hours.
Utilize Shield to maintain platform visibility
Salesforce’s user-friendly development capabilities make it ideal for enabling bespoke apps but make it difficult for compliance teams. Shield, fortunately, can assist you in keeping track of a wide range of data.
Event Monitoring, for example, allows you to monitor detailed use statistics, while Encryption safeguards data and Field Audit Trail records its condition and value for up to ten years. If you need assistance, a variety of third-party services are available to help you put Shield into action. In addition to analyzing the Salesforce security architecture, it’s vital to properly identify and categorize the data in your Salesforce Org since categorization greatly impacts access restrictions.
Secure your APIs
Salesforce has the interesting advantage of being simple to integrate with other services and apps, allowing you to exchange data and increase functionality. However, not all of the apps you connect to Salesforce are secure, which may lead to a variety of problems, including,
- Code injections
- DDoS assaults
- Fraudulent logins
- Replay attacks
- Unsecured cardholder information,
- Exposed data through URI keys.
Because using an unprotected or shady API might result in compliance concerns, data breaches, and hacks, precautions must be taken to use these APIs while being safe.
You may take the following steps:
- Enable whitelisting on the app
- Create an integration user
- Improve access limits for your integration users
- Monitor API access.
Use custom login flow
Salesforce helps safeguard against unauthorized logins while granting authorized access even in odd circumstances. For instance, suppose a user attempts to log in outside of business hours or from a restricted IP address.
In that case, it may initiate a flow that the user must complete in order to obtain access, such as answering secret questions, for further security. If the login attempt is unexpected, you can add an authentication step with a bespoke login flow.
Utilize App Whitelisting to Prevent Data Leaks to 3rd Party Apps
You may also keep Salesforce secure by setting App Whitelisting for your organization. This prevents users from accidentally providing third-party apps access to your organization’s data. Salesforce admins may use this functionality to control which third-party apps can access the org. This solution is scalable since it may be installed for the entire org for all Salesforce users or for certain users only if necessary.
Enabling App Whitelisting
- Enroll in QuantoKnack’s Salesforce admin training to learn how to request this option from Salesforce support.
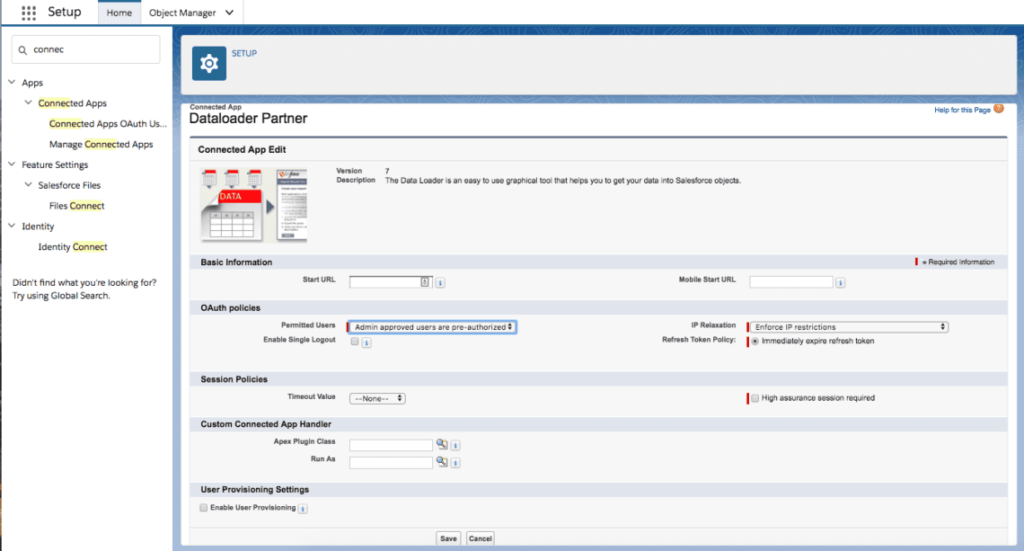
- After you’ve activated the functionality, navigate to Manage Connected Apps. Then, if you want to whitelist beneath the app, click ‘Edit.’ • Navigate to OAuth policies > Permitted Users. Now, choose the “Admin-approved users are pre-authorized” option.
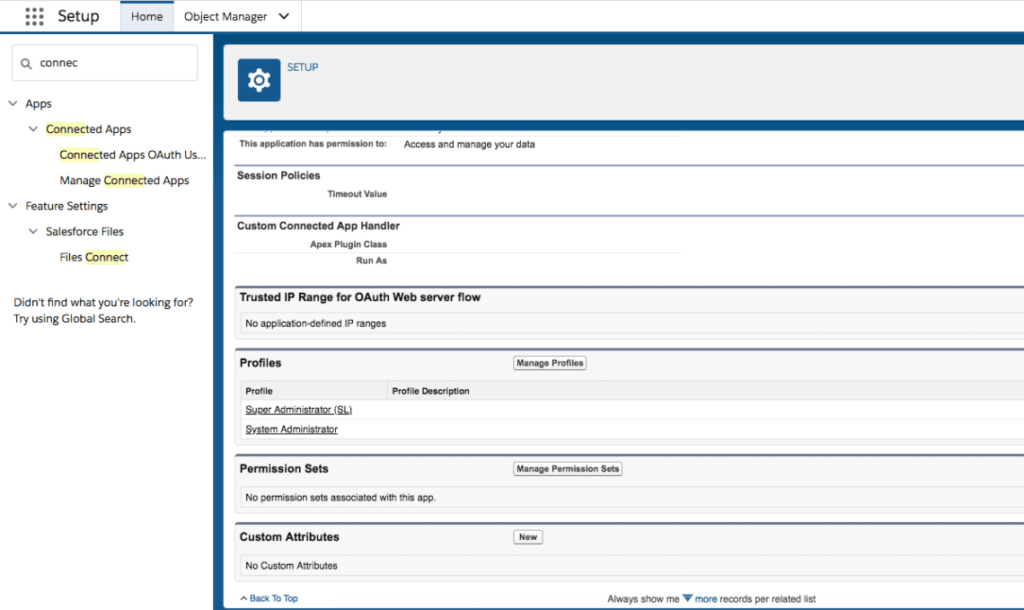
- Go back to Manage Connected Apps and choose the app you whitelisted. This will take you to the app’s details, where you may configure Permission Sets and Profiles.
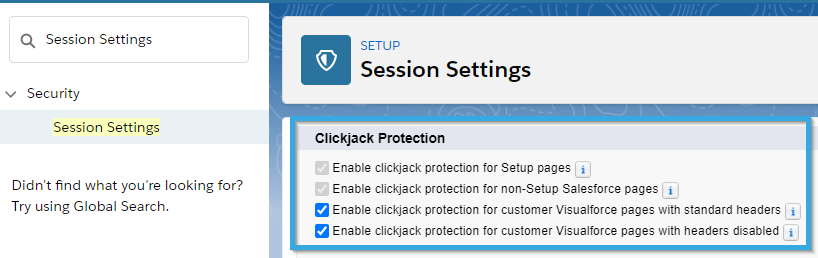
Use Clickjack Protection
Clickjacking is the technique of tricking users into clicking on legitimate-looking URLs that execute harmful operations, such as changing your Salesforce data without your permission.
While Salesforce protects against clickjacking by default, you may strengthen these safeguards by checking all checkboxes in the Clickjack Protection section in Setup > Security > Session Settings.
Use Strong Password Policies
Our final simple Salesforce data security victory is to improve your password policy. While you don’t have to make your password requirements overly stringent (people will be unhappy if they have to establish new passwords every few days), you can still improve your security with minor tweaks.
Here are some recommended options (which may be changed in Setup > Security > Password Policies):
- Password length: 15 characters (the default for Salesforce is 8).
- Password complexity: alpha, numeric, and special characters must be included.
- Password Expiration: 90 days
- Password question: Cannot contain a password (if users set the answer to their security question as their password, anyone could gain access to their account)
- Passwords should be backed up with MFA if you follow this tutorial, which means that these settings will considerably limit the odds of compromised accounts.
Conclusion
While Salesforce provides adequate data protection, there is no harm in going the extra mile.
Remember that a developer is only a facilitator for the company. Salesforce administrators, on the other hand, are individuals who are well-versed in business processes and can assist developers in understanding the appropriate solution design.
Salesforce administrators are the foundation of the entire CRM process. They should have greater resources and freedom to realize the CRM function’s potential fully.
Enroll in QuantoKnack’s Salesforce Admin Course and Salesforce Developer Training program now if you want to advance your career or get the most out of the Salesforce platform for your organization. Our Salesforce admin training can help you advance your career in top IT firms across the world.
Allow our industry experts to assist you in mastering the Salesforce platform and preparing you for the future by using real-world projects! You will be working on a project at the end of the Salesforce Admin program, and QuantoKnack will certify you as a ‘Salesforce Administrator’ depending on the project you submit.
Don’t miss the chance this chance! Register with QuantoKnack today to learn from prominent Salesforce experts in live training sessions and become certified as a “Salesforce Admin.”